Coronavirus or Computer Virus: Hikvision Senior Director of Cybersecurity on Phishing Hacks and Malware, and Tips to Avoid Them
In this blog, Hikvision Senior Director of Cybersecurity Chuck Davis discusses phishing hacks and malware related to the coronavirus, and tips to avoid them.
As the COVID-19 coronavirus becomes a global concern, cybercriminals are leveraging this tragedy to spread their own kind of virus and digital attacks to prey on the fears of people around the world.
What is Happening?
Attackers are using phishing campaigns to target businesses and individuals. One example, reported by BleepingComputer, shows how scammers created a phishing email with World Health Organization (WHO) logos in an effort to trick recipients into clicking a link that supposedly will give them online training but in fact, asks them to create an account on their imposter site. When the person "creates an account" the scammers now have an email address and a password that they can use to try and log into Facebook, Twitter, LinkedIn, Gmail, Office365 and any other site they can think of. They do this because people tend to reuse passwords across multiple accounts. This is known as a credential stuffing attack.
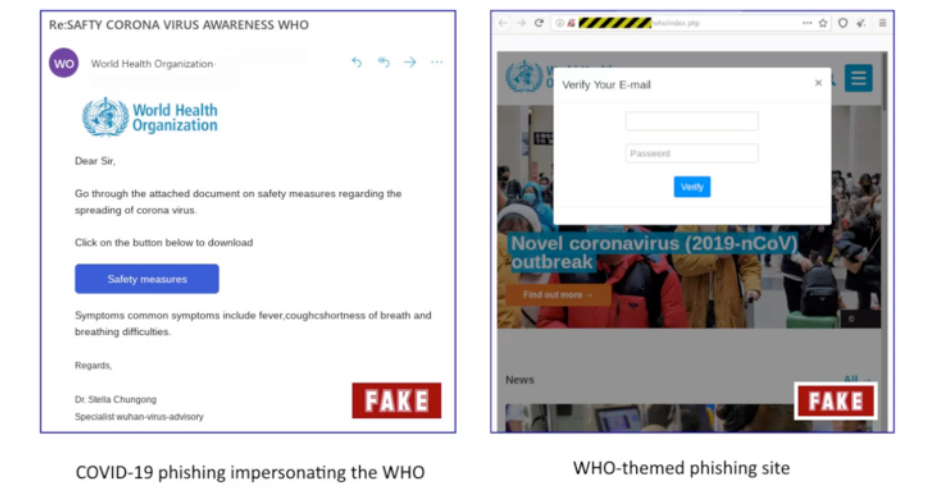
Bleeping Computer example of a credential-stealing phishing email that is crafted to look like it comes from the World Health Organization
The WHO is not the only organization that is being spoofed. Last week, researchers at cybersecurity company, COFENSE reported the following phishing campaign that appears to be from the CDC. The email subject, "COVID-19 - Now Airborne, Increased Community Transmission" creates a sense of fear and urgency. The body of the email states that, "...three new cases have been confirmed around your area today" and provides a link to the CDC website for more information.
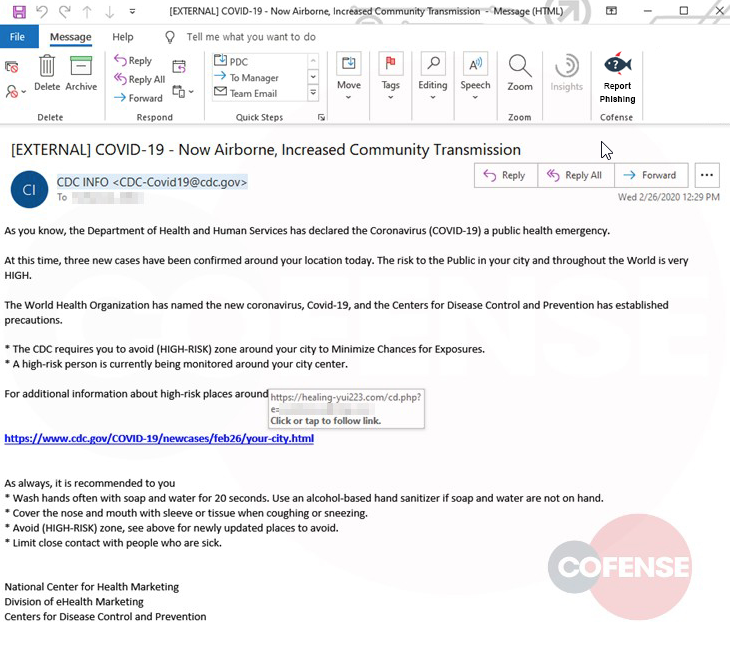
Cofense example of phishing email that looks to be sent from the CDC.
If someone clicks on that link (and many will) it redirects the victim to an Outlook-themed landing page that is hosted by the attacker. When the victim enters their Microsoft credentials, the page redirects the victim to the actual CDC site so the victim is unaware that they just gave away their login credentials to the attacker.
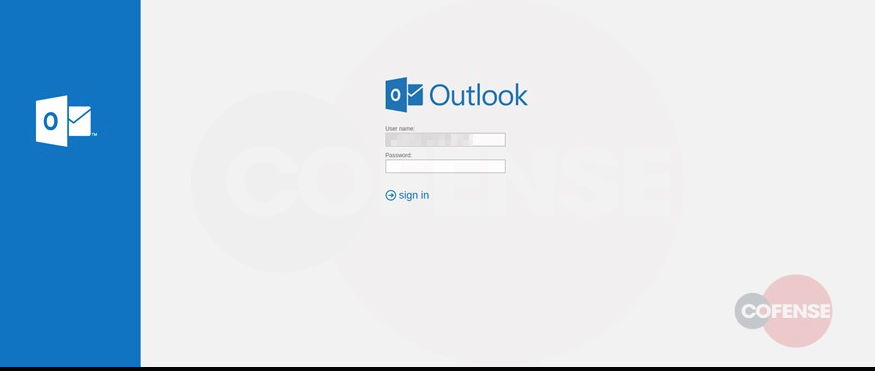
Cofense example of malicious Outlook-themed login page that is managed by the phishing attacker.
However, not all attackers are phishing for your login credentials. Some of them want to access your computer.
Last week, Threatpost reported that one malware campaign was using a COVID-19-themed phishing attacks to trick victims into installing malware. The attackers sent a phishing email with a PDF attachment that offers tips on coronavirus safety. When the pdf file is opened, named “CoronaVirusSafetyMeasures_pdf,” it installs a remote access Trojan (RAT) which gives the attacker full remote access to the victim's computer without the victim knowing it.
Earlier this week, cybersecurity reporter Graham Cluley wrote about security researchers at Malwarebytes who have found malicious code in a website that, "appears to have copied the look-and-feel of a legitimate Coronavirus map from Johns Hopkins University." The malicious code skims the victim's computer for passwords and payment card details.
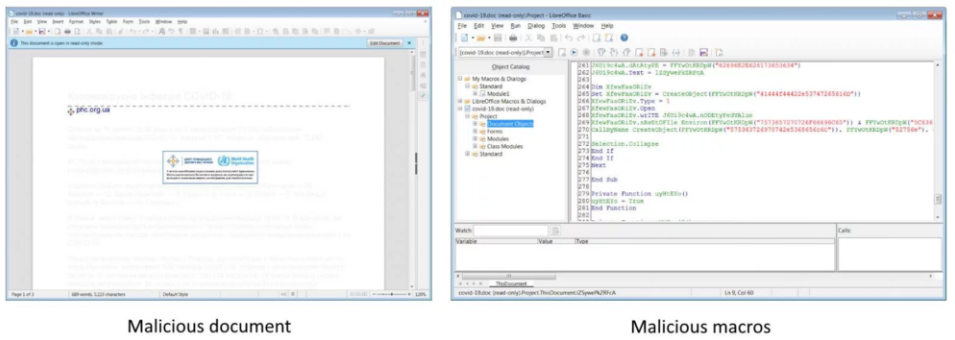
Finally, Bleeping Computer reported that researchers from MalwareHunterTeam, "found a three-page Coronavirus-themed Microsoft Office document containing malicious macros, pretending to be from the Center for Public Health of the Ministry of Health of Ukraine, and designed to drop a backdoor malware with clipboard stealing, keylogging, and screenshot capabilities." The picture below shows the malicious document and the malicious macros that are embedded in that document.
What Can You Do?
These phishing attacks are no different than the ones you get in your inbox regularly. They are just preying on a timely circumstance.
- Remember that your Inbox is a dangerous place. It is the easiest and most effective way for an attacker to get past your home or company's firewall and network security.
- Understand basic and advanced phishing attacks by reading this Hikvision blog on the subject.
- Read the Federal Trade Commission's tips on Identifying and reporting COVID-19 scams
- Read the World Health Organization's tips on identifying and reporting scams.
- The United States Computer Emergency Readiness Team (US-CERT) recommends the following ways to minimize your chances of becoming a victim of phishing attacks:
- Filter spam
- Don’t trust unsolicited email
- Treat email attachments with caution
- Don’t click links in email messages
- Install antivirus software and keep it up to date
- Install a personal firewall and keep it up to date
- Configure your email client for security
Phishing is used in 90 percent of data security breaches and is the leading method that attackers use to gain access to home and company networks and systems. While you may want to donate to a charity or learn about updates on the spread of COVID-19, be sure to go to trusted websites like the Centers for Disease Control and Prevention and the World Health Organization directly. Don’t get there by clicking on links in email, in order to prevent becoming a victim of phishing hacks and malware.
