Cybersecurity in the Workplace: Hikvision Cybersecurity Director Discusses Spear Phishing

As part of NCSAM (National Cybersecurity Awareness Month), Chuck Davis, Hikvision’s director of cybersecurity for North America is sharing weekly cybersecurity information designed to help better secure our homes, our workplaces, and the global Internet at large.
On October 15 we talked about cybersecurity at home, and then we discussed protecting yourself online. This week we are going to talk about cybersecurity in the workplace and focus on "spear phishing."
In previous blog posts, we have discussed phishing emails and how to identify them. You can read those blog posts here and here.
Today we are going to address a special kind of phishing attack called spear phishing. Targeted to a specific person or organization, spear phishing emails typically have information about the victim in the email that makes the email seem credible.
Recent Examples of Spear Phishing Campaign
A prominent example of spear phishing occurred during the 2016 presidential campaign. A Philadelphia Inquirer report, says that John Podesta, chairman of Hillary Clinton's presidential campaign, received "a misleading email that looked like a security notification from Google, asking Podesta to change his password by clicking an embedded link ... Podesta followed the email's instructions, changing his password and giving hackers access to 50,000 of his emails."
Another spear phishing method has to do with financial information. Earlier in 2018, a law firm posted a blog that gave the following example:
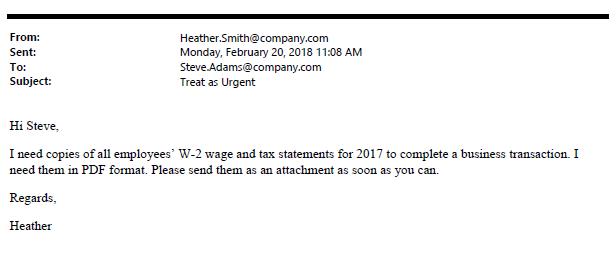
Another, newer attack method involves extortion. Lately, a handful of friends and colleagues said they received an email claiming that a malicious hacker had installed malware on their computer. The email showed a valid password belonging to the recipient, and explained that the attacker has access to the recipient’s webcam and has a log of their keystrokes. The attacker gives the recipient two choices:
- Ignore the email and the attacker will send something embarrassing to all of the recipient’s contacts.
- Or, pay a ransom in bitcoin, and the hacker will delete everything they have.
This email scam has been a popular spear phishing attack in 2018. As cybersecurity reporter, Brian Krebs, blogged about in July, “Here’s a clever new twist on an old email scam that could serve to make the con far more believable.”
If you happen to receive one of these emails, don’t panic. This is a scam.
How Did Attackers Get a Valid Password?
At a high level the attacker is using old lists of known usernames and passwords that were harvested from data breaches like LinkedIn, Adobe, etc. and posted, shared and sold on the dark web. This data has been floating around the Internet for years in some cases. But, because many people reuse passwords, they may still be using an old password on some sites. Next week, we'll include a more in-depth description of a spear phishing attack.
What Can Victims Do?
If you receive an email like this, there are some things you can and should do. Below is a list of those recommended actions:
- If this is a business email address, let your cybersecurity team know immediately about the threatening email. There could be an ongoing company-wide campaign that the cybersecurity team can stop. If the cybersecurity team is aware of the campaign they can also help educate employees.
- Visit https://haveibeenpwned.com/ This site is hosted by a respected cybersecurity professional named Troy Hunt. Make sure to enter all work and personal email addresses, and subscribe to get updates. If your email address is ever found in a data breach, you will be alerted. They won’t have every data breach, but if there are a large number of usernames and/or passwords posted to the dark web, the site will likely add that list and email you if your username/password has been part of that data breach.
- Use two-factor authentication (2FA) or multi-factor authentication (MFA) everywhere possible.
- Use a password manager. This will allow you to make great passwords (20 plus characters) that are unique for every website. And, you won’t need to remember any of them.
- Never reuse passwords. If you have reused passwords, take time to change them now, before it’s too late. Threat actors buy up username/password lists and start trying to login with the username and password on other sites, like Twitter, Facebook, and Spotify.
- If you are alerted that a password has been compromised, change it immediately and see item number three, above.
- Be skeptical about incoming email. Read the following phishing blog to learn more on how to identify phishing attacks.
- Be wary of short URLs. Malicious links are sometimes sent in short URLs through social media. Check short URLs with a tool like checkshorturl.com to preview the real address before clicking.
- Be aware of doppelganger domains, which are domain names that look like a valid, trusted domain like “goog1e.com.” If you don’t look closely at URLs sent in email, you could quickly overlook this.
Check back next week for more details on what an extortion attack could look like.
