Email Phishing Examples from Hikvision’s Director of Cybersecurity: Part II
Steps to Avoid Malware Attacks From Email Phishing, Top 7 Tips From US-CERT
Hikvision’s director of cybersecurity, Chuck Davis, together with the Hikvision Security Lab at Hikvision headquarters, is leading the cybersecurity program for Hikvision North America, overseeing all internal and external cybersecurity initiatives and programs in the region. In part two of a blog about phishing, Davis provides examples of phishing attack methods, as well as tips to identify phishing emails and prevent becoming a victim of attacks.
Phishing has long been an effective way for attackers to trick people into divulging sensitive information or infecting a system with malware. Malware can give an attacker remote access to protected systems and networks, encrypt a user’s data and charge a ransom to decrypt the data, or use that system as part of an attack against other systems. A critical part of malware defense is identifying a phishing attack.
Example of Masking a URL
In our previous blog, we looked at a URL in a real phishing email that was not masked in any way. We mentioned that this is very easy to do. In this post, we further examine the email and show methods regularly used by attackers, to trick even the most clever and cybersecurity-aware email consumers. Below is an example of how easy it can be to mask a URL. If you hover over the link below, you'll notice that it does not link to yahoo.com, but rather, to google.com.
Clickjacking: Advanced URL Masking
Hovering over a URL is a popular and somewhat effective way to scrutinize a URL but it’s not 100 percent effective. A more advanced phishing attack will use methods like clickjacking. Clickjacking shows that the URL is pointing to one destination address, but takes the user to another address.
In this example, notice when you hover over the URL it shows the destination address as Google's homepage. However, if you click on the link, you will see that it actually takes the user to Yahoo's. Clickjacking is done by inserting a small piece of JavaScript behind the URL that directs a user to a specific address when they click!
International Domain Name (IDN) Homograph Attack
In our last example of advanced phishing attacks, we will talk about IDN Homograph attacks. This is done by using characters from different language alphabets that look the same as the Latin/English characters. In this example, apple.com was registered using Cyrillic characters instead of the Latin/English characters. They look exactly the same, but are very different.
A security researcher registered the above domain. You can read his blog post here.
Clicking the Link
Let’s get back to our original example from the last blog and look at what happens if you are tricked. After clicking the link, you can see below that the URL has changed to yet another domain name. This time it begins with “login.comcast.net” but again, notice the trailing forward slash does not appear until much later in the URL, which means that the domain name for this page is actually "o7b.name."
Phishing Websites Vs. Verified Websites
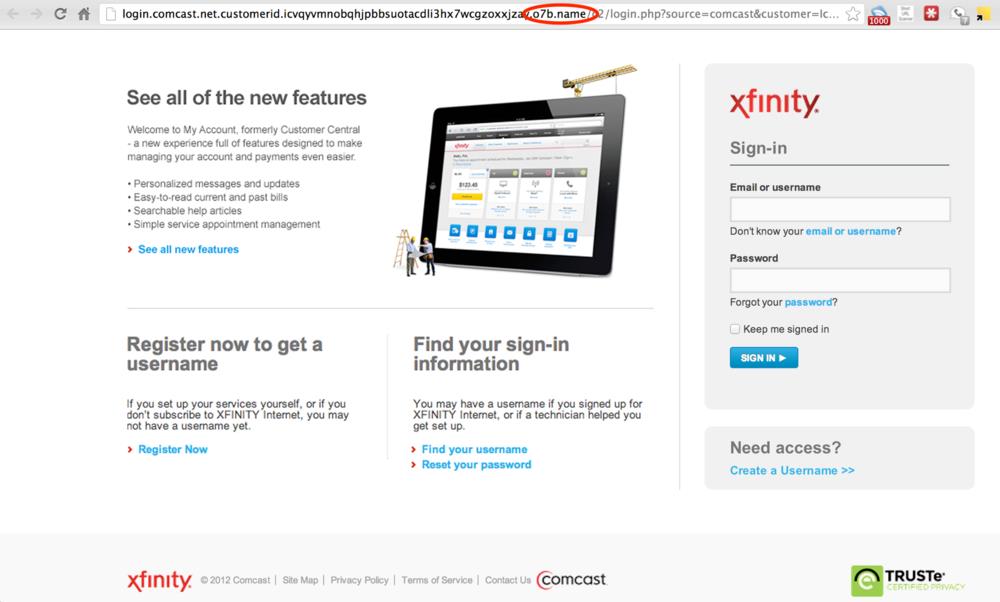
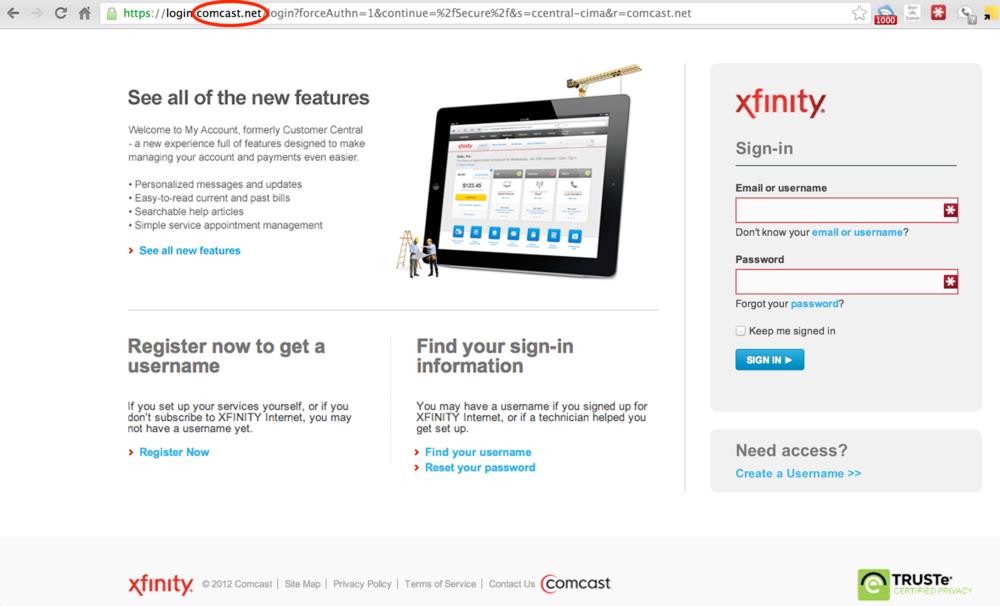
The next thing to note here is that the rogue site looks very much like the actual Comcast Xfinity authentication page. Below, compare the screenshots of the rogue site and the actual Comcast Xfinity page. They are nearly identical!
The rogue site:
The real site:
Two Steps To Reduce Risk of Phishing Attack
While it is increasingly difficult to identify a well-crafted phishing email, there are some steps that can be taken to reduce the risk of falling victim to a phishing attack.
- Look carefully at the email headers. Check the "From" and "To" fields for anything suspicious. While we already stated that these can be spoofed, they can also be a good first indicator of a suspicious email. Here is how to check the full email headers in Gmail: https://support.google.com/mail/answer/29436?hl=en
- Hover over links and be sure to read the entire URL: When you hover over a link, notice if the website link is different than the listed URL. Also inspect the entire URL from the first forward slash, back to the left, to see where that link is actually going. For example, http://www.google.com.search.us/query.html is actually going to a server called "search.us," not google.com. Again, this can be spoofed in some cases but it’s a good indicator of how phishing links can appear to be sites we trust.
Top Seven Tips to Avoid Becoming a Phishing Victim
The following tips from the United States Computer Emergency Readiness Team (US-CERT) provide recommendations of ways to minimize your chances of becoming a victim of phishing attacks:
- Filter spam.
- Be wary of unsolicited email.
- Treat email attachments with caution.
- Don’t click links in email messages.
- Install antivirus software and keep it up to date.
- Install a personal firewall and keep it up to date.
- Configure your email client for security.
While phishing has become an effective way for hackers to get individuals to divulge sensitive information or infect a system with malware, taking precautions and following the steps above can minimize security concerns.
For additional examples of phishing, click here to read Part 1 of this blog. For more Hikvision cybersecurity blogs, visit us online.

