Hikvision Cybersecurity Director Discusses Password Management Strategies, Using Password Managers to Reduce Security Concerns

In our recent blog, Hikvision discussed the challenge of creating complex passwords and provided three rules for creating good ones to reduce security concerns and hacking risks.
In that blog, we talked about how we all hate passwords and how the cybersecurity wonks tell us that we have to do unreasonable things like:
- Make passwords so complex that we can’t possibly remember them (long and multiple character sets)
- Make a unique password for every one of the tens or hundreds of sites and applications that we use. Oh, and they all have to be long and strong which means we won’t remember them.
Today we are going to explore how you can achieve this and actually make your digital life more secure and much easier than when you had to remember all of those passwords or look them up on a spreadsheet on your computer’s desktop. Welcome the Password Manager!
First, we’ll look at an overview of common password management strategies below, then discuss password managers as a tool in more detail.
Common Password Management Strategies
Below are some of the common password management strategies that people use today:
- Reusing simple passwords (i.e. monkey123), which is high risk because it is easy to guess (by guessing, I mean using a super-fast password cracking/guessing tool).
- Reusing complex passwords (i.e. My dog likes to eat at 8 a.m.). This is high risk because while the password is good, if anyone guesses or learns it, they can use it on other sites as well. For example, if your LinkedIn password is discovered, the bad guys/gals will try that username and password on every social media and popular website to see if you used it elsewhere.
- Saving unique passwords in an unencrypted document or spreadsheet on your computer. While you are protected against someone getting access to your passwords document unless they are logged into your computer, if someone does get access to your files or malware gives access to an attacker, then it is game over.
- Creating unique but predictable complex passwords for each account (i.e. Facebook**pw4224). These are good passwords, but expect that if someone gets one of your passwords, they can likely figure out the rest of your passwords.
- Writing all of your passwords in a book and keeping it locked up. If the book is properly secured, then this might be low risk. Locked in a desk at your house is much better than locked in a desk at work. However, if there is a fire or flood, you would lose all of your passwords.
- Using a password manager with unique, complex passwords for every site. This is low risk. The risk here is if you forget your master password or if someone else gets your master password. More details about password manager tools below.
The Password Manager: A Tool to Reduce Password Security Concerns
A Password Manager is a software tool that is used to store all of your passwords in an encrypted file so that you, and no one else, have very easy access to them, helping to minimize security concerns. Most modern password managers have additional features such as cloud storage, auto-filling fields, and password generators that make very good passwords.
The cloud storage feature of password managers provides easy access to your passwords from different devices. While it sounds scary to have all of your passwords stored online, a good password manager will encrypt all of your password data before it is uploaded to the cloud and will make sure that only you have the keys (the master password that you set) to decrypt your passwords on each device. All of this security is great unless you forget your master password. In that case, you would lose everything.
The autofill feature is convenient because when you go to a site, such as LinkedIn, the password manager’s browser plugin recognizes the URL and sees the username and password fields then enters your username and password automatically. This is not only convenient, but it also helps defend against keystroke login malware, that could learn and share your passwords. It also ensures that your username and password are not entered into a doppelgänger domain website, like 1inkedin.com rather than LinkedIn.com. This feature has however been abused and used for some creative attacks. By hiding the username/password fields on a web page that are not viewable by the person visiting that page, some attackers have been able to harvest account credentials. This Wired article goes into greater detail about this type of attack.
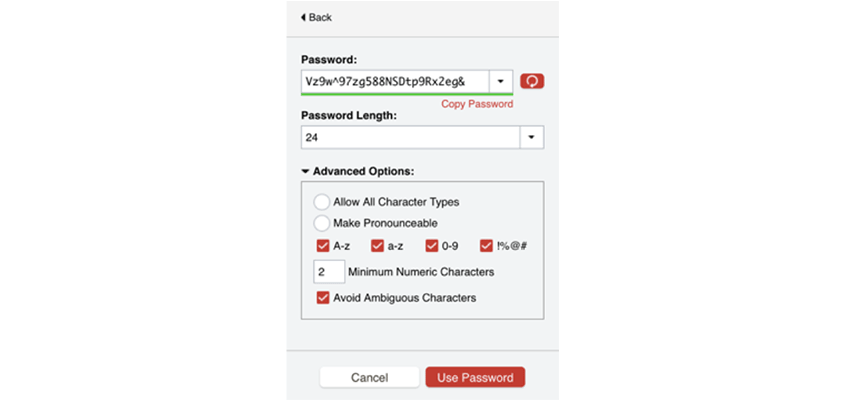
The password generator is a very important part of this whole solution. The password manager can’t help you much if you create simple passwords such as 12345678 or monkey123. So, the password manager will recommend passwords for you and if you accept them when creating an account, it will automatically store that in your password manager. For example, here is a screenshot from the password generator in LastPass. You can see that it is 24 characters and is using all four-character sets (uppercase, lowercase, numbers, and special characters) to create a difficult password to guess and a nearly impossible password to remember. Good thing you don’t need to remember this password!
There is certainly debate over the problems with password managers: What if you forget your master password, or what if someone gets your master password and uses it to hack your account? These are valid questions, however, with the rapid growth of account compromises and data security breaches, the risk seems far greater for someone is using simple passwords and trying to remember them or reusing those passwords on multiple accounts.
Here are a few articles that compare and contrast the leading password managers.
- PC Magazine: The Best Password Managers for 2019
- Wired: Get A Password Manager. No More Excuses.
- Life Hacker: The Five Best Password Managers
- Consumer Reports: Everything You Need to Know About Password Managers
In closing, I’ll say that password managers will greatly help to secure your accounts, but are they enough? In the next blog post about passwords, I’ll explain Multi-Factor Authentication (MFA), and how and why you should use it almost everywhere you can.
