Hikvision’s Director of Cybersecurity Outlines Examples of Phishing
Common Malware Attacks Using Email Phishing
Hikvision’s director of cybersecurity, Chuck Davis, together with the Hikvision Security Lab at Hikvision headquarters, is leading the cybersecurity program for Hikvision North America, overseeing all internal and external cybersecurity initiatives and programs in the region. Below he provides an overview of phishing, a common cyber threat, including examples and a link to recommendations to prevent malware attacks.
Phishing attacks have long been an effective way for attackers to trick people into divulging sensitive information or infecting a system with malware. Malware can give an attacker remote access to protected systems and networks, encrypt a user’s data and charge a ransom to decrypt the data, or use that system as part of an attack against other systems.
In March of 2017, Google stated that its machine learning models now can detect and stop spam and phishing with 99.9 percent accuracy. However, this is a cat and mouse game that has been played for years by the spammers/phishers on one side, and the spam filter developers on the other side. Once the defenses get better against the latest spam attack methods, the spammers change their tactics to bypass the filters.
Examples of Phishing With Email Spam
Here is an example of a fairly obvious spam email that Google’s filter caught and placed in the spam folder of a Gmail account. There is no subject line; there is just a link. When Google discovers rogue links, the red box shown in the email below serves as a warning to not click on links or reply with personal information.
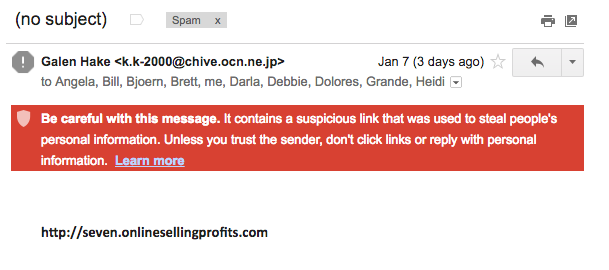
While most of the spam email that is sent to you will never reach your inbox, the ones that do, are getting much more difficult to detect.
The following is an example of a phishing email that made it through spam filters back in 2012, one of the first phishing emails Davis received that he felt was very effective. This attack attempted to steal login credentials for the recipient's Comcast account.
Phishing Email Example Number Two
The following email appears to come from “Customer Central,” an email address using the domain name, “comcast.com.” Of course, this was spoofed. The "from" field cannot be trusted in this case, and is not actually showing you the source of the email.
By masking the full destination email address, the email also creates heightened security concerns. In the image below, it appears the email was sent to “pllpt.” This is grayed out and in small text. While that could be a mailing list, one would expect something different if it was sent directly from Comcast.
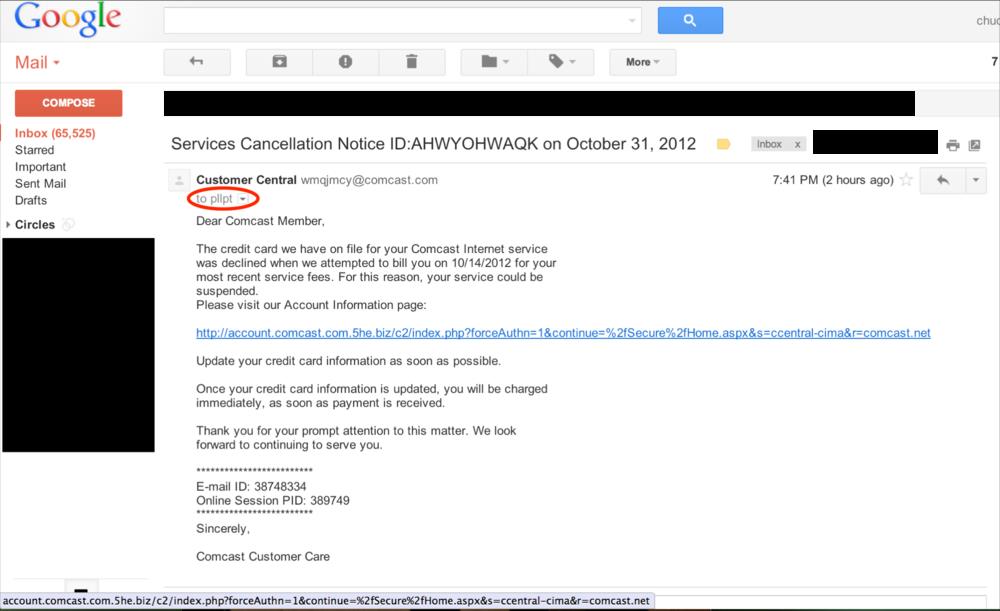
The email indicates that the customer’s credit card information on file has declined the payment, and the email requests that the recipient update his or her credit card information by clicking on the link.
A quick or casual review of this link may seem safe. The URL begins with, account.comcast.com.
But when one looks at the rest of the URL we see something out of the ordinary: account.comcast.com.5he.biz/
The last two sections before the forward slash (/) indicate the domain name of the destination. In this case, the domain name is actually 5he.biz. The “account.comcast.com” is all subdomains of 5he.biz.
Interestingly, the author of this phishing email did not try to mask the actual link, which is easy to do and might be a little more effective in tricking someone to click on it.
Davis recommends individuals filter spam emails and be cautious about unsolicited emails with links in them. When in doubt, copy and paste the URL into a preview site like richpreview.com or for short URLs, paste them into a site like checkshorturl.com to see the full URL and preview the site.
For more examples of malware attacks using phishing and tips to reduce security risk, visit this link. For more cybersecurity tips from Davis, click here.
Now you know how to better identify and scrutinize a link before clicking on it. Part two of this blog will show what happens when you click on the link in the above example. We will also show some advanced phishing tactics that are not well known, and show examples of how hovering over a link is not always a successful way to preview the URL.

