Part Two: An Overview of Spear Phishing Hacks by Hikvision Senior Director of Cybersecurity

Learn to Identify Phishing Attacks to Prevent Becoming a Victim, Plus 8 Tips to Protect Yourself Online
Being able to identify phishing email scams can reduce your risk of becoming a victim to this cyberattack. In yesterday’s HikWire blog, Hikvision’s senior director of cybersecurity, Chuck Davis, overviewed examples and types of phishing scams. In today’s blog, Davis will discuss a special type of phishing hacks called spear phishing.
Yesterday, we noted that phishing scams have risen since the onset of the pandemic. And, Barracuda networks found a 667 percent rise in coronavirus-driven phishing attacks in February 2020.
Understanding these attacks will help prevent you becoming a victim to them. Continue reading below to learn more and check out tips to stay safe from phishing attacks.
What is Spear Phishing?
Spear phishing is a type of phishing attack that is targeted to a specific person or organization. Spear phishing emails typically have information about the victim in the email that makes the email seem credible.
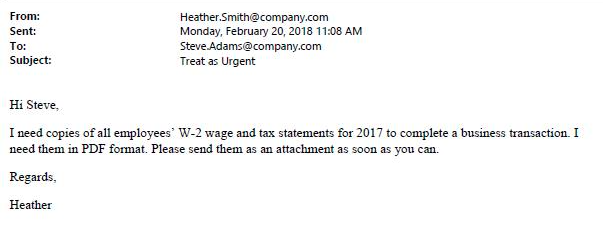
Here is a spear phishing example that has to do with attempting to gain financial information. In 2018, a law firm posted a blog that gave the following example, which appears to be from an internal person within the company.
Another type of attack method involves extortion. Victims report receiving an email claiming that a malicious hacker installed malware on their computer. The email shows a valid password belonging to the recipient, and explains that the attacker has access to the recipient’s webcam and has a log of their keystrokes. The attacker gives the recipient two choices:
Ignore the email and the attacker will send something embarrassing to all of the recipient’s contacts.
- Or, pay a ransom in bitcoin, and the hacker will delete everything they have.
- If you happen to receive one of these emails, don’t panic. This is a scam.
8 Tips to Protect Yourself Online
Below are several steps you can take to reduce your risk of becoming a victim to phishing attacks, and boost cybersecurity.
- If this is a business email address, let your cybersecurity team know immediately about the threatening email. There could be an ongoing company-wide campaign that the cybersecurity team can stop. If the cybersecurity team is aware of the campaign they can also help educate employees.
- Use two-factor authentication (2FA) or multi-factor authentication (MFA) everywhere possible.
- Use a password manager. This will allow you to make great passwords (20 plus characters) that are unique for every website. And, you won’t need to remember any of them.
- Never reuse passwords. If you have reused passwords, take time to change them now, before it’s too late. Threat actors buy up username/password lists and start trying to login with the username and password on other sites, like Twitter, Facebook, and Spotify.
- If you are alerted that a password has been compromised, change it immediately and see item number three, above.
- Be wary of short URLs. Malicious links are sometimes sent in short URLs through social media. Check short URLs with a tool like checkshorturl.com to preview the real address before clicking.
- Be aware of doppelganger domains, which are domain names that look like a valid, trusted domain like “goog1e.com.” If you don’t look closely at URLs sent in email, you could quickly overlook this.
- Visit https://haveibeenpwned.com/. This site is hosted by a respected cybersecurity professional named Troy Hunt. Make sure to enter all work and personal email addresses and subscribe to get updates. If your email address is ever found in a data breach, you will be alerted.
Hikvision routinely posts articles about trends in cybersecurity, including steps you can take to protect your data and accounts from hacks and vulnerabilities. Visit our cybersecurity blog link regularly for updates. And, check out our online Cybersecurity Center for resources such as best practices, changing passwords, and updating Hikvision product firmware.
