Cybersecurity at Home: Hikvision Cybersecurity Director Talks Network Security and Network Segmentation
Hikvision Observes Cybersecurity Awareness Month
October is National Cybersecurity Awareness Month (NCSAM), and Hikvision USA is pleased to join with the Department of Homeland Security and other businesses to help raise cybersecurity awareness. A collaborative effort between the U.S. government and industry, the goal of NCSAM is to ensure that all Americans have the resources they need to stay safe and more secure online.
As part of NCSAM, Chuck Davis, Hikvision’s director of cybersecurity for North America is sharing cybersecurity information designed to help better secure our homes, our workplace and the global Internet at large.
This week we are going to talk about network security and network segmentation. Over my career, in addition to teaching computer science at the undergraduate and graduate levels at numerous universities, I have also created and managed some corporate cybersecurity education programs. In both I've found that getting the more critical concepts across to people is most effective when the message is personalized and can be applied at home as well as in their work.
Why Network Segmentation Makes Sense in Your Home
Network segmentation is a simple concept that has been used by network administrators for decades, but only recently have we seen a real need to apply this concept in the home. There are a number of contributing factors:
- The rapid growth of Internet of Things (IoT) devices being added to home networks.
- The various levels of experience, support, and cybersecurity “baked into” these devices.
- The high bandwidth needs of streaming services, like Netflix and Hulu, plus all of the additional IoT devices, is putting a strain on older home firewalls/routers.
A typical home network has one firewall router as shown below. This might be something purchased at Best Buy, Frye’s, Amazon or another retailer, or something sold by an Internet Service Provider.
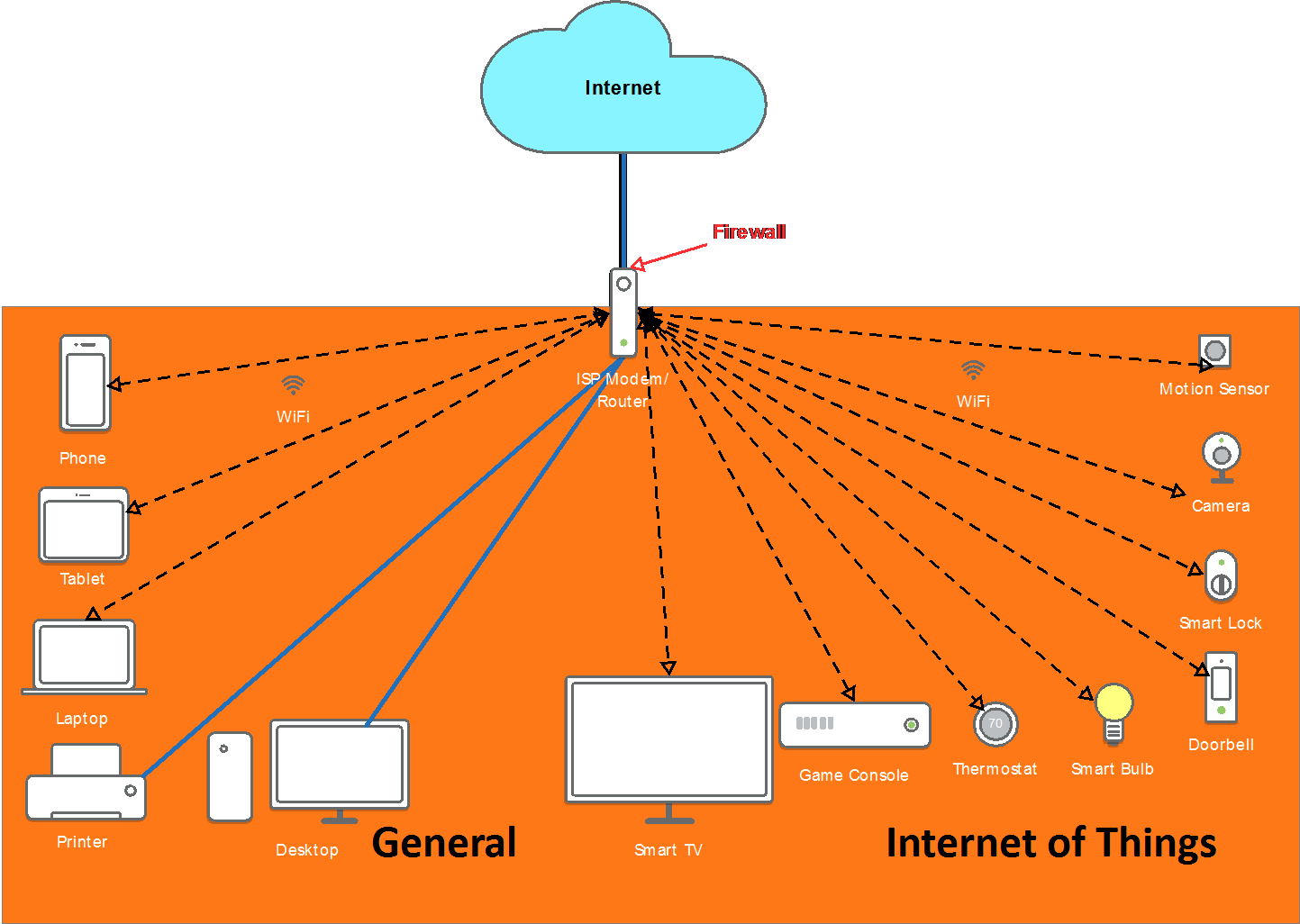
This is called a flat network because there is no firewall or logical separation between any of the devices, so they can talk directly to every other device on the network.
This architecture was good when most homes just had a few computers—in the late 90s and early 2000s when mom and dad and two kids each had a laptop or desktop. In this era, people listened to mp3 players that synced music through a laptop and flip phones were all the rage. While some of these devices could access Internet data through a computer, they didn’t have Wi-Fi, or any direct access to the Internet.
The Smartphone Changed Everything
Then came the birth of the smartphone. Wi-Fi phones became prevalent and, in many situations, doubled the number of computers connected to the home router.
Next came smart TVs, smart light bulbs, smart refrigerators, and the age of the IoT. According to a 2017 study, North Americans have an average of 13 devices per person. That means a family of four has an average of 52 devices on their network. That may seem high, but most Americans don’t realize how much their home network has grown over the past 10 to 15 years, and they don’t realize that all of those “things” are actually computers. All of these devices have a network interface, storage, memory, processors and an operating system. Additionally, they are always connected to the Internet and are rarely patched.
Fundamental Risk of Flat Network
Many IoT devices are just small, Linux computers put in things like light bulbs, refrigerators and thermostats. Most of these devices don’t allow for automated patching and some don’t even allow manual patching. Because of this, it is fundamentally risky to keep all of your devices on a flat network.
One recent example is when a cybercriminal gained access to an Internet connected thermometer in the lobby of an unnamed casino. Once they got access to the thermometer, the attackers were able to pivot the attack and gain access to the high roller database and "then pulled it back across the network, out the thermostat, and up to the cloud." This likely would not have happened with the appropriate network segmentation, firewalls and security controls.
Benefits of a Segmented Home Network
Network segmentation is a way to isolate devices on separate networks to achieve better sharing of throughput or bandwidth to the Internet, securing systems with more sensitive data, and separating systems from people and other systems that don’t have a need to connect to them.
In the typical home, this can be achieved by using two more routers. You can see in the diagram below that they are plugged into the main router using standard ethernet cables. Both of the new routers offer wired and wireless connectivity. The network on the left is used for normal computing devices, including smartphones, laptops, printers, backup drives and any devices that have more sensitive data. This is also where you would create a guest network for visitors to your house. Built-in guest networks are great so that you can give Internet access to guests without giving them network access to your other computers or printers.
The network on the right is the IoT network. This is where you put devices that don’t store sensitive data and may not be updated regularly because the functionality doesn’t exist or because manual patching happens only when the owner of those devices can remember to do it.
Isolating Problems By Segmenting Networks
Another benefit to this architecture is more efficient use of bandwidth. Many people back up their laptops and desktops to network drives. Imagine that this backup is happening automatically in the evening when the laptop isn’t being used. At the same time, the parents are watching a movie on Netflix while one of them is printing a large document. One of the children is watching YouTube videos and the other is playing a video game on an Xbox. In the architecture above, all of that traffic runs through the one home router. In the below architecture, all the backups and printing happen behind the router on the left and the streaming is all run through the router on the right.
From a cybersecurity perspective, network segmentation works to isolate problems. If a laptop gets infected with malware, it won’t be able to get to the IoT network because the firewall is in front of that IoT network. The same is true if an IoT device is compromised; the firewall on the general network will protect it from malware infected IoT devices in the same house, because of the firewall.
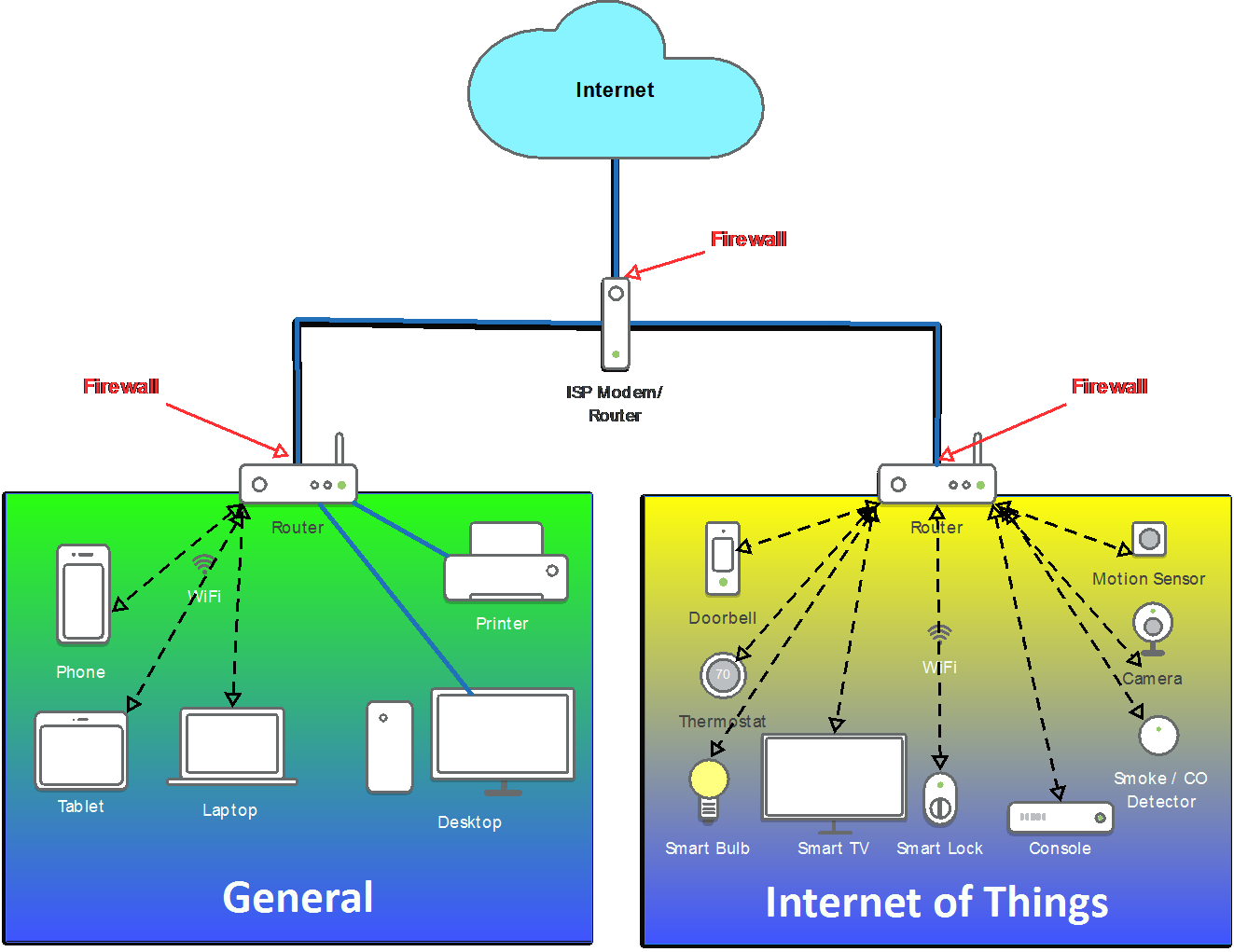
Of course, additional routers could be added if one would like to extend the layers of trust. Consider putting TVs and game consoles are on separate networks from light bulbs and thermostats. Or put devices that get automatic updates on a separate network from those that don’t. That way if your smart fish tank thermometer is hacked, it can’t get to your backup drive.
Check back next week, when we'll take a look at applying some of these concepts in the work environment.

