Hikvision Cybersecurity Director Outlines 3 Rules for Creating Good Passwords to Reduce Security Concerns and Hacking Risks
Hikvision Cybersecurity Director Outlines 3 Rules for Creating Good Passwords to Reduce Security Concerns and Hacking Risks
Hikvision’s director of cybersecurity, Chuck Davis, has authored numerous blogs about cybersecurity best practices, ways to reduce vulnerabilities, and tips to prevent malware attacks. In today’s blog, Davis outlines the rules to creating good passwords so you can reduce security concerns and the risk of being hacked.
Below, Davis offers insights for password creation, with tips and tricks to create unique, complex passwords for every site without having to remember each one.
Long Passwords, Short Memories
The password is something we all love to hate. Many of us have to create hundreds of passwords and we’re told by the paranoid cybersecurity experts to make them long and use all of the character sets on your keyboard so that they are not easy to guess. This also makes them difficult to remember, so what do most people do? They re-use passwords—which is also a big no-no.
While we all know these general rules, most people don’t know why they exist and what the real risks are. In this blog, I will help you understand the importance of following the rules when developing your list of passwords.
Three Tips for Creating a Good Password
Below are three tips for creating complex and hard-to-hack passwords.
- Make them long: There is some debate over the best minimum length of a password. Analysis from security expert, Troy Hunt, has shown that many of the sites we use do not require very long passwords. However, research from Georgia Tech Research Institute (GTRI) shows that the longer the password, the better. Even back in 2010, Richard Boyd, a senior researcher at GTRI said, “Eight-character passwords are insufficient now… and if you restrict your characters to only alphabetic letters, it can be cracked in minutes.” Another GTRI research scientist involved in the project, Joshua L. Davis, said that, “any password shorter than 12 characters could be vulnerable -- if not now, soon.” As computing power increases, the number of characters in a "long password" will increase as well.
- Strong password have multiple characters: Use all four character sets including uppercase letters, lowercase letters, numbers and special characters. In most cases, spaces are also allowed, which means you can use a sentence as your password or passphrase.
The reason you should follow this rule is due to a certain password-cracking tool that uses a rainbow table—a database of possible passwords and their associated hash. We’ll talk more about rainbow tables in a subsequent blog post but for now, to explain rainbow tables, let’s imagine you have a dictionary of words, without the definitions, that contains all English words in only lowercase letters. That’s a pretty thick book. Now stack on top of that a dictionary of all English words in only uppercase letters. It would make the stack twice as high. Now add to the stack, a book filled with all numbers from 0 to 99999999. Each of these books represents a rainbow table of possible passwords. In a computer, each of these databases is very large but they can be managed with a laptop and a large amount of storage. Now imagine if you had one book that had all three of those dictionaries, plus every word in mixed-case and with numbers substituting letters, combined together. For example, the word “bat” might have the following options:
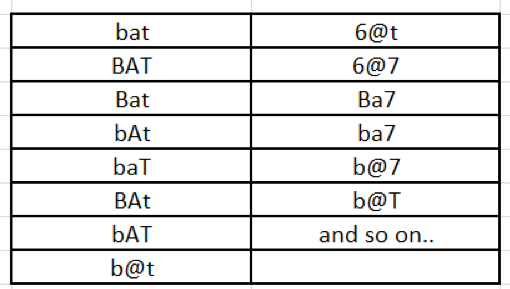
So you can see that creating an eight character, all-lowercase password could be a relatively quick exercise for a hacker to crack with minimal effort and computing power. However, if you created a 20-character password with all the character sets, it would be quite difficult to crack due to the size of the rainbow table and the computing power needed to execute the attack.
- Create a unique password for every login: Creating unique passwords for every account is very important. The reason is that if an attacker discovers your password for one account, they are likely to try that password for other popular online services and could gain access to all of your accounts. The advice to create unique passwords for every site and every application is sound, but since most people don’t know why that is recommended, they tend not to follow it. But with so many data breaches happening nowadays, your account information has likely been compromised for one site or another. When those databases of cracked usernames, email addresses and passwords are posted to the Internet, threat actors will take something such as a LinkedIn email address and password, and attempt to use it on Facebook, Twitter, Google, Instagram, Snapchat and any other popular website they can think of to see if it works there as well.
Be Alerted if Your Email is Part of a Security Breach
A tip to help you identify if you have been the victim of a security breach is to visit Haveibeenpwnd.com and enter your email address. This site is hosted by a respected cybersecurity professional named Troy Hunt. Make sure to enter all work and personal email addresses, and subscribe to get updates. If your email address is ever found in a data breach, you will be alerted. They won’t have every data breach, but if there are a large number of usernames and/or passwords posted to the dark web, the site will likely add that list and email you if your username/password has been part of that data breach.
Recap of Top Password Rules
So let’s recap. We are supposed to create a password for every website that is:
- More than 20 characters long
- Uses uppercase and lowercase letters, numbers, and special characters
- Is unique and never reused
This is an unreasonable request given that many of us have more than 100 passwords. So how can we follow the rules and reduce our risk of being hacked? The answer is a password manager. In an upcoming blog post, we will discuss password managers and how to use them so you can reduce your security concerns.

